Last year was a year of many "Firsts" for me. It meant saying yes to things that seemed scarey, getting out of my comfort zone because only then could I grow and taking small leaps of "Faith". Despite it all, one thing remained constant - my love for books. The changes in my life meant … Continue reading Year 2022 in Book Review
Year 2021 in Book Review
In the beginning of 2021 and having read 18 books in 2020, I set a SMART goal of completing 24 books. Besides, I had formed a habit out of it, enjoyed the downtime it gave me and as an insatiable learner, I found it rewarding in every way. At the end of it all, I … Continue reading Year 2021 in Book Review
Building my Home Lab part 4: deploying the domain controller and endpoints
In the previous section, we looked at deploying the hypervisor, firewall and router. This part focuses on emulating a realistic office network consisting of multiple endpoint OSs. The aim is to deploy one system each as a template that we can then clone to their respective networks as needed. We will setup an active directory … Continue reading Building my Home Lab part 4: deploying the domain controller and endpoints
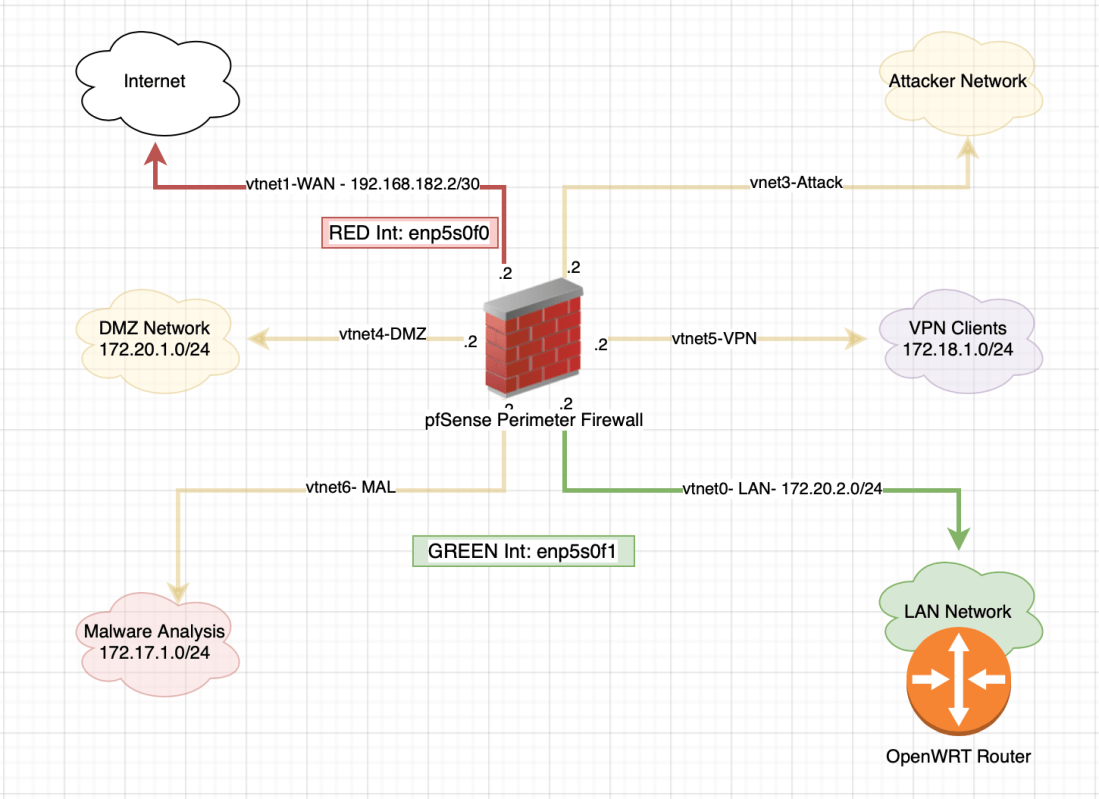
Building my Home Lab part 3: deploying the core infrastructure (hypervisor,firewall and router)
Let's continue with our lab upgrade project. So far, we've assembled the hardware and hopefully come up with a good enough architectural network design to get us started. Our next step will be to deploy the core infrastructure which will be made up of the hypervisor, firewall and router. For those new to the term, … Continue reading Building my Home Lab part 3: deploying the core infrastructure (hypervisor,firewall and router)
WriteUp: HackTheBox Bashed
Bashed is a Linux machine rated easy. We gain access to the user flag via basic enumeration. To get the root flag, we have to escalate privileges by taking advantage of a scheduled cron job that can run without a password being required. Table of Contents ReconnaissanceEnumerationUser FlagPrivilege EscalationRoot FlagDefender's Note Reconnaissance We start off … Continue reading WriteUp: HackTheBox Bashed
Building my Home Lab part 2: Architecture
In the first part of my homelab upgrade series, we assembled the hardware for the homelab. Our next step is to design the network topology and come up with an appropriate network addressing scheme. We also need to have a rough idea of what we intend to do with the different network segments. The lab … Continue reading Building my Home Lab part 2: Architecture
WriteUp: HackTheBox GrandPa
GrandPa is a windows machine rated easy. The machine is running a vulnerable version of IIS which we are able to exploit and gain access, however, the user we have is not a system user. We end up having to migrate to another user, exploit yet another vulnerability to escalate privileges into system. As system, … Continue reading WriteUp: HackTheBox GrandPa
WriteUp: HackTheBox Optimum
My next HackTheBox machine to play around with is Optimum. It is a Windows system running HTTP File Server and rated easy. As the machine is running a vulnerable version of HFS, we are able to exploit a vulnerability and gain user access to the box. Inorder to get the root flag, we take advantage … Continue reading WriteUp: HackTheBox Optimum
WriteUp: HackTheBox Nibbles
My fourth box to play around with in HackTheBox is Nibbles. It is a Linux machine rated easy. Scanning the box shows two open ports, SSH and HTTP. Following the HTTP route, we are able to gain access to the server. As the user has permissions to run a file without requiring a password, we … Continue reading WriteUp: HackTheBox Nibbles
WriteUp: HackTheBox Jerry
This being my third box on HackTheBox, we are able intercept the communication and using brute force, gain access to the Windows Server via easily available default credentials. Once on the server, we spin up a reverse shell that gives us system access. From there on, it's smooth sailing to the flags. Table of Contents … Continue reading WriteUp: HackTheBox Jerry